Identity and Access Management (IAM) is a set of policies, processes, and technologies that organizations use to manage and control access to their systems, applications, data, and resources. IAM ensures that only authorized users can access the information and resources they need to do their jobs while protecting sensitive information and resources from unauthorized access.
IAM provides a centralized system for managing user identities and access privileges, which helps organizations to streamline their security operations, reduce security risks, and comply with industry regulations.
The core components of IAM are:
- Authentication: The process of verifying a user’s identity through a set of credentials, such as a username and password, biometric data, or security tokens.
- Authorization: The process of granting or denying access to resources based on a user’s identity and access privileges.
- Directory Services: A central repository of user identities and access privileges, which is used to authenticate and authorize users.
- Provisioning: The process of creating, modifying, and deleting user accounts and access privileges, based on changes in an organization’s requirements.
- Federation: The process of allowing users from different organizations to access resources on a shared network, without requiring separate authentication.
- Audit and Reporting: The process of monitoring user activities and generating reports on access privileges, usage, and security incidents.
IAM can be implemented through a variety of technologies, such as access management systems, single sign-on (SSO) solutions, multi-factor authentication (MFA) systems, and privileged access management (PAM) solutions.
Single Sign-On(SSO)
Single sign-on (SSO) is a type of authentication process that allows users to log in to multiple applications and systems using a single set of credentials, such as a username and password. With SSO, users do not have to remember multiple usernames and passwords for different applications, which can simplify the login process and improve productivity.
In a typical SSO setup, the user authenticates once, typically using a strong form of authentication such as multi-factor authentication (MFA), and then gains access to multiple applications and systems without having to re-enter their credentials. The SSO system stores the user’s authentication credentials securely and passes them on to other systems and applications as needed.
SSO is typically implemented using one of two methods: federation or directory-based authentication. Federation allows users to access resources on a shared network, without requiring separate authentication. Directory-based authentication uses a central directory, such as Active Directory, to store user credentials and manage access to resources.
Benefits of SSO include improved security, increased productivity, and reduced helpdesk costs. By reducing the number of passwords that users need to remember, SSO can improve password security and reduce the risk of password-related security incidents. SSO can also improve productivity by reducing the time that users spend logging in to different applications and systems. Finally, SSO can reduce helpdesk costs by reducing the number of password-related support calls.
SSO can be implemented through a variety of technologies, such as Security Assertion Markup Language (SAML), OpenID Connect, and OAuth. SSO is widely used in enterprise environments and is becoming increasingly popular in consumer applications as well.
MFA (Multi-factor Authentication)
Multi-Factor Authentication (MFA) is a security mechanism that requires users to provide multiple forms of authentication to access a system or resource. MFA enhances the security of authentication by requiring users to provide at least two different types of credentials, such as a password and a security token or biometric data, before granting access.
The goal of MFA is to prevent unauthorized access to systems and resources, even if an attacker gains access to a user’s password. With MFA, even if a password is compromised, an attacker would still need access to the second factor of authentication to gain access to the system or resource.
There are three types of authentication factors:
- Knowledge Factors: Something that the user knows, such as a password or a PIN.
- Possession Factors: Something that the user has, such as a security token, a smart card, or a mobile device.
- Inherence Factors: Something that the user is, such as biometric data, like fingerprints, facial recognition, or voice recognition.
MFA can use a combination of these factors to authenticate a user. For example, a user may be required to provide a password (knowledge factor) and a security token (possession factor) to access a system or resource. Alternatively, a user may be required to provide a fingerprint scan (inherence factor) and a smart card (possession factor) to gain access.
MFA is an essential security mechanism that helps prevent unauthorized access to systems and resources, particularly for sensitive data and applications. Organizations should consider implementing MFA for all critical systems and resources, and require MFA for remote access and other high-risk scenarios.
Privileged Access Management (PAM)
Privileged Access Management (PAM) is a set of policies, processes, and technologies used to control and monitor access to critical systems, applications, and data within an organization. PAM is designed to reduce the risk of security breaches, data leaks, and cyber-attacks caused by privileged users who have access to sensitive data and resources.
Privileged users are those who have elevated access privileges, such as system administrators, database administrators, network engineers, and other IT personnel. These users have access to critical systems and resources that contain sensitive data, which makes them prime targets for cyber-attacks. PAM provides a way to manage and monitor privileged user access, reducing the risk of security breaches.
The core components of PAM include:
- Privileged Account Discovery: Identifying and inventorying all privileged accounts in an organization, including system accounts, application accounts, and service accounts.
- Privileged Account Management: Managing and securing privileged accounts by enforcing strong passwords, regular rotation of passwords, and monitoring access to these accounts.
- Privileged Session Management: Recording and monitoring all privileged user sessions to detect and prevent unauthorized access to critical systems and data.
- Privileged Access Governance: Ensuring compliance with industry regulations and best practices by enforcing policies, tracking access, and providing audit trails for privileged users.
PAM is typically implemented using specialized software solutions that provide centralized management and control of privileged user access. PAM solutions can automate many of the tasks associated with managing and securing privileged access, such as password management, access control, and session recording.
PAM is an essential security mechanism for organizations that deal with sensitive data and critical systems. By controlling and monitoring privileged user access, organizations can reduce the risk of security breaches and data leaks caused by privileged user abuse or cyber-attacks.
In this post, we will be looking at how best to handle identity and access management in AWS. In AWS, IAM is a web service that enables you to manage access to AWS services and resources securely.
IAM Best Practices
Here are some best practices for IAM in AWS:
1. Use the principle of least privilege
The principle of least privilege means that you should grant users and applications the minimum permissions necessary to do their jobs. This reduces the risk of accidental or intentional misuse of permissions and limits the potential damage that can be caused by a security breach.
To apply the principle of least privilege, you should:
- Define a set of policies that specify the minimum permissions necessary for each role and user.
- Use IAM groups to manage permissions for users that have similar needs.
- Regularly review permissions and remove unnecessary permissions.
2. Enable MFA for all users
Multi-factor authentication (MFA) is a security feature that requires users to provide two or more forms of authentication to access AWS resources. Enabling MFA for all users, including root users, is a best practice that adds an extra layer of security to your AWS account.

3. Use IAM roles instead of IAM users
IAM roles are a more secure way to grant access to AWS resources than IAM users. IAM roles are similar to IAM users in that they have a set of permissions associated with them. However, roles are not associated with a specific user account and can be assumed by any authorized user or service.
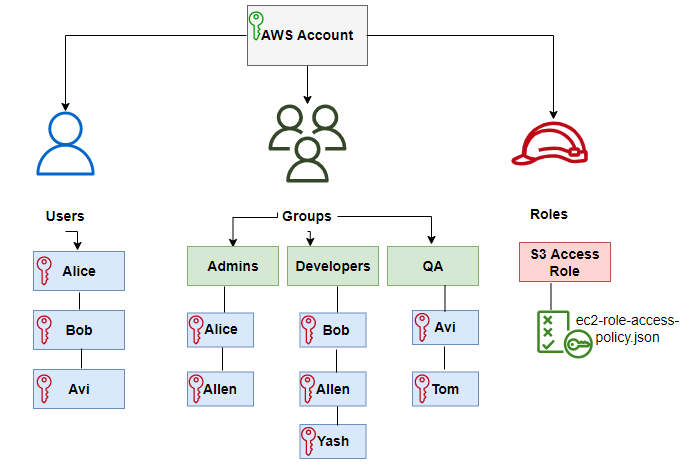
Using IAM roles instead of IAM users has several advantages:
- You can easily grant and revoke permissions to a role, without having to manage individual user accounts.
- You can define trust relationships between roles, which allows you to grant permissions to resources in different AWS accounts or to external resources.
- You can use roles to delegate permissions to AWS services, such as Lambda or EC2 instances, without having to store access keys and secret access keys in the instance or function code.
4. Use IAM policies to enforce security policies
IAM policies are a set of rules that define the permissions and restrictions that apply to IAM users and roles. IAM policies allow you to enforce security policies that control access to AWS resources.
To create effective IAM policies, you should:
- Define policies that specify the minimum permissions necessary for each role and user.
- Use IAM groups to manage permissions for users that have similar needs.
- Regularly review permissions and remove unnecessary permissions.
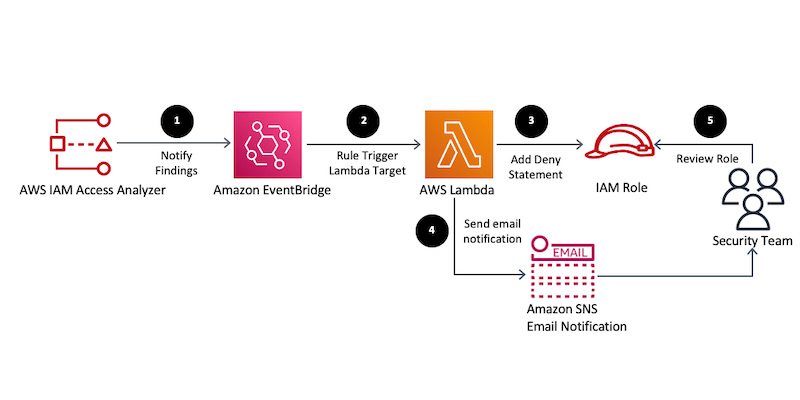
5. Use IAM access analyzer to detect unintended resource access
IAM Access Analyzer is a feature of AWS IAM that enables you to identify unintended access to your resources. IAM Access Analyzer uses automated reasoning and logic to identify resource policies that could allow unintended access to resources.
IAM Access Analyzer analyzes resource policies for S3 buckets, Lambda functions, KMS keys, IAM roles, and CloudTrail trails. When IAM Access Analyzer identifies a policy that could allow unintended access, it provides you with a recommendation to resolve the issue.
Access Analyzer provides several features to help you detect unintended access:
- Policy validation: Access Analyzer analyzes the policies that control access to your resources and checks them against a set of known vulnerabilities and best practices. It identifies potential issues in your policies that may allow unintended access.
- Policy recommendation: Access Analyzer provides you with recommendations on how to update your policies to address any issues found in the validation process. The recommendations can be easily applied to the policies using the AWS Management Console or the AWS Command Line Interface.
- Resource coverage: Access Analyzer provides comprehensive coverage of resources that can be accessed in your AWS environment. It supports the analysis of policies for S3 buckets, Lambda functions, KMS keys, IAM roles, and CloudTrail trails, among others.
- Continuous monitoring: Access Analyzer continuously monitors your resource policies to detect changes that may affect security. It alerts you if a change is made to a policy that may allow unintended access.
To use Access Analyzer, you need to enable the service in the AWS Management Console. Once enabled, Access Analyzer begins analyzing your resource policies and providing you with recommendations. You can view the recommendations in the Access Analyzer dashboard, where you can also take action to apply the recommendations to your policies.
6. Regularly rotate access keys and passwords
Regularly rotating access keys and passwords is a best practice that helps to reduce the risk of unauthorized access to AWS resources. Access keys and passwords should be rotated at least every 90 days.
7. Monitor IAM activity using AWS CloudTrail
AWS CloudTrail is a service that enables you to monitor and audit your AWS account activity. CloudTrail records all actions taken by IAM users, roles, and AWS services, and stores the data in an S3 bucket.
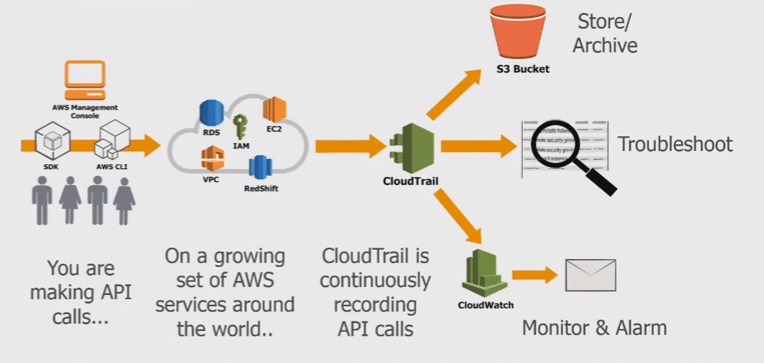
Monitoring IAM activity using CloudTrail helps you to:
- Identify and respond to security threats.
- Detect and investigate security incidents.
- Meet compliance requirements.
Achieving better IAM using terraform
Infrastructure as code (IaC) is an approach to managing IT infrastructure by defining and managing infrastructure resources in code. IaC can be used to achieve better identity and access management (IAM) on AWS by allowing you to define IAM resources, such as roles, policies, and users, in code and deploy them using automation.
Here are some ways that IaC can be used to achieve better IAM on AWS:
- Consistency: By defining IAM resources in code, you can ensure that they are consistent across environments. This can help prevent configuration drift and ensure that all resources are configured in the same way. This is because the same code is used to create, update, and delete your IAM resources. You can use Terraform to create a new AWS environment from scratch, or you can use it to modify an existing environment by applying changes to your Terraform configuration. This approach ensures that your IAM policies and roles are always in sync with your infrastructure.
- Version control: IaC code can be version controlled, which makes it easy to track changes and roll back to previous versions if necessary. This can be especially useful when managing complex IAM configurations. This means you can define your IAM policies and roles in a text file, which can be version-controlled, tested, and reviewed just like any other code. You can use modules to define reusable policies and roles, and you can use variables and data sources to parameterize your IAM policies and roles.
- Continuous compliance and auditability: Using Terraform to define IAM policies and roles allows you to continuously monitor and audit your AWS environment. You can use Terraform to create reports that show the current state of your IAM policies and roles, and you can use Terraform to apply changes to your policies and roles as needed. This ensures that your AWS environment remains compliant with your security and compliance policies.
- Collaboration: IaC code can be shared and collaborated on by teams. This can help teams work together to develop and manage IAM resources, and it can ensure that everyone is working with the same configuration.
- Role-based access control: Terraform allows you to define IAM roles and policies that enforce role-based access control (RBAC). RBAC is a security model that restricts access to resources based on the roles and responsibilities of users. You can use Terraform to define IAM policies that grant access to specific resources based on the user’s role. This approach ensures that users only have access to the resources they need to perform their jobs.
- Automation: IaC code can be deployed using automation, which can save time and reduce the risk of errors. This can be especially useful when deploying large IAM configurations or when deploying changes to multiple environments.
To use IaC to achieve better IAM on AWS, you can use a tool like Terraform or AWS CloudFormation to define IAM resources in code. These tools allow you to define IAM roles, policies, and users in a declarative syntax that can be version-controlled and deployed using automation.
For example, you could use Terraform to define an IAM policy that grants access to an S3 bucket:
resource "aws_iam_policy" "s3_policy" {
name = "s3_policy"
policy = jsonencode({
Version = "2012-10-17"
Statement = [
{
Effect = "Allow"
Action = [
"s3:GetObject",
"s3:PutObject"
]
Resource = [
"arn:aws:s3:::example-bucket/*"
]
}
]
})
}
This code defines an IAM policy that allows the user to perform the s3:GetObject and s3:PutObject actions on objects in the example-bucket S3 bucket. This policy can be version-controlled and deployed using automation, ensuring that the policy is consistent across environments and reducing the risk of errors.
Risks of not handling IAM properly
Identity and Access Management (IAM) is an essential part of any organization’s security posture since it is the practice of controlling who has access to what resources within an organization’s network.
However, the risks of not handling IAM properly can be severe and far-reaching. Here are some of the most critical risks associated with IAM mismanagement.
- Unauthorized access to sensitive information: One of the primary risks of not handling IAM properly is unauthorized access to sensitive information. Without proper authentication and authorization controls in place, anyone within the organization or outside of it can gain access to sensitive data, which can result in financial and reputational damage.
- Data breaches: Data breaches are another significant risk associated with mismanaging IAM. A data breach can occur when an attacker gains access to sensitive information by exploiting a vulnerability in the IAM system. This can result in the exposure of confidential data, financial loss, and damage to an organization’s reputation.
- Compliance violations: Organizations that fail to handle IAM correctly may also face compliance violations. Many regulations, such as the GDPR, require organizations to implement appropriate measures to protect personal data. Failure to comply with these regulations can result in significant fines and legal action.
- Account hijacking: Account hijacking is another significant risk of IAM mismanagement. Hackers can gain access to user accounts by stealing login credentials, which can result in unauthorized access to sensitive information, data breaches, and other security incidents.
- Internal threats: IAM mismanagement can also lead to internal threats. Employees with malicious intent can use their access to sensitive information to steal data or cause other security incidents. Without proper IAM controls in place, it can be challenging to detect and prevent these types of threats.
- Lack of accountability: Organizations that fail to handle IAM properly may also lack accountability. Without proper audit and monitoring controls, it can be challenging to track who has access to sensitive data and when. This can make it difficult to identify and remediate security incidents.
- Increased operational costs: Mismanaging IAM can also lead to increased operational costs. For example, when users are not properly authenticated or authorized, IT teams may spend more time troubleshooting issues and resolving security incidents. This can result in additional labor costs and lost productivity.
- Damage to brand reputation: Finally, the risks of not handling IAM properly can also damage an organization’s brand reputation. Data breaches and other security incidents can result in negative publicity, loss of customer trust, and reduced sales.


 Is GitOps worth the hype? (ArgoCD)
Is GitOps worth the hype? (ArgoCD)
 DevOps and Artificial intelligence - how a DevOps team take advantage of AI and ML
DevOps and Artificial intelligence - how a DevOps team take advantage of AI and ML
 Security in cloud native
Security in cloud native